Proofpoint Targeted Attack Protection SaaS Defense
Protection against malicious files in SaaS file stores
TARGETED ATTACK PROTECTION SAAS DEFENSE
Safeguard your organization against hidden threats in cloud-based file-storage apps.
Sorry, this product is no longer available, please contact us for a replacement.
Key Benefits
- Detect known and unknown threats in SaaS files
- Detect URL threats embedded in files
- Get visibility into the size, scope, and type of threats
- Identify users affected by threats hidden in SaaS files
- Deploy quickly into key SaaS apps
Proofpoint Targeted Attack Protection SaaS Defense detects malicious files in Google Drive, OneDrive, SharePoint, and Box to safeguard your organization against hidden threats in cloud-based file-storage apps.
Software-as-a-service (SaaS) is a security blind spot for most enterprises. Users routinely store, access, and share files without knowing where they came from or whether they’re safe. At the same time, security teams have little visibility into these threats. Files are usually accessible only after logging into the service, making sandboxing and other analysis techniques impractical. And domain-reputation services can leave you a false sense of security, as most major SaaS services are legitimate, even if the files they contain aren’t.
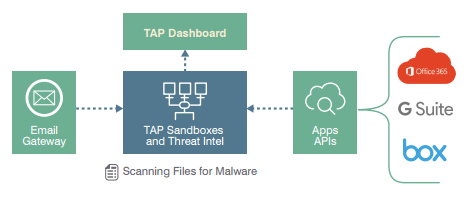
Protection against malware and phishing files in SaaS apps
SaaS Defense, part of our Targeted Attack Protection family of products, helps you take a “trust, but verify” approach to SaaS-hosted files and how your people use them. As files are added to SaaS services from within your environment, SaaS Defense “detonates” them in our sandbox to observe and analyze. Our multilayer analysis detects potential threats by examining behavior, code, and protocol in multiple stages through a combination of static and dynamic techniques.
Attackers vary their tactics to avoid detection, and some attacks don’t use malware at all. Threats such as email fraud (also known as business email compromise or whaling) and credential phishing leave no obvious traces. That’s why our technologies also include logic to learn from both malware-based and malware-free attacks. In every attack, we observe the content, patterns, tactics, behaviors, and tools to make the next one easier to catch.
Gain visibility into the size, scope, and type of threats you face
No other security company gives you as much visibility into the threats that matter. Our threat intelligence spans email, network, mobile apps, social media, and SaaS platforms. Our threat graph of community-based intelligence contains more than 500 billion data points. That means we can correlate attack campaigns across diverse industries and geographies. Using this broad base of threat data, we attribute most malicious traffic to campaigns, and these are surfaced in our TAP dashboard. You can easily distinguish between broad-spectrum attacks and those targeted at executive leadership or other high-value employees.
TAP SaaS Defense also draws on insight from Proofpoint Emerging Threats (ET) Intelligence, the timeliest and most accurate source of threat intelligence in the market. Proofpoint ET Intelligence is the gold standard for threat researchers, offering fully verified threat intelligence with context beyond domains and IP addresses.
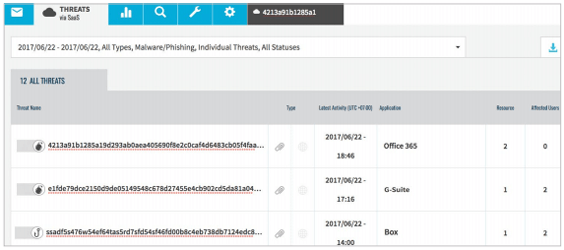
Find users affected by threats hidden in SaaS files
Proofpoint TAP SaaS Defense gives you complete visibility through the TAP Dashboard. Our web-based interface gives you graphical indicators of the types of threats, SaaS application hosting the malicious content, the number of threats found, and the number of affected users. Drill-down visibility provides data at organizational, threat, and user levels to help you prioritize alerts and act on them. The TAP dashboard provides detailed forensic information on both individual threats and campaigns is available. TAP SaaS Defense requires TAP URL or Attachment Defense.
We help answer critical questions, such as:
- What is the threat and what type of threat is it?
- Who and how many people are exposed to the threat?
- What forensics can I use to tell if an endpoint has been compromised?
Deploy quickly into key SaaS applications
To protect your people, data, and brand, your security tools must work where your people do, at the pace that they do. The TAP SaaS Defense architecture enables you to deploy quickly and derive value right away. You can protect a handful to hundreds of thousands of users with a simple API integration. You’ll see results in hours or days—not weeks or months.
To protect your people, data, and brand, your security tools must work where your people do, at the pace that they do. The TAP SaaS Defense architecture enables you to deploy quickly and derive value right away. You can protect a handful to hundreds of thousands of users with a simple API integration. You’ll see results in hours or days—not weeks or months.
Documentation:
Download the Proofpoint Targeted Attack Protection for SaaS Datasheet (PDF).
